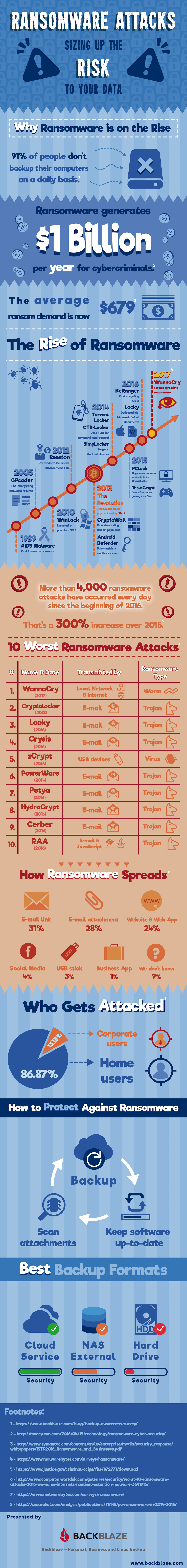
The Danger
In recent years there has been a large rise in the worldwide incidence of a specific type of malware known as “Ransomware”. For those unfamiliar with the term, ransomware refers to a type of malicious software infection that holds your data hostage until a requested amount of money is paid. There are several variations but most commonly this is done by encrypting your documents so they are unusable and demanding payment in Bitcoin currency to provide the decryption key to unlock your stuff.
While one could then pay the ransom and hopefully get the decryption key, there is NO guarantee you will receive it and get your data back. Additionally, whether they cough up the decryption key or not, this just encourages the ransomers and allows them more resources to continue their criminal activity. I do NOT recommended this as a solution.
No, the BEST way to deal with this situation is to have a backup system in place that is capable of dealing with a ransomware attack in such a way as to get you back up and running as quickly as possible while denying any gain to the perpetrators.
Time to get paranoid
Everybody knows backing up is important for routine data safety and should be done (hard drives do fail after all) but, depending on your method and backup setup, it could still leave you open to the effects of ransomware. Most ransomware will scan your computer and look for any attached devices (like the external hard drives many use for backing up) or networked storage (such as office file servers) and encrypt those files as well. So the danger of having both your main copy of the data AND your backups affected by ransomware can be very high depending on your network and storage configuration.
Graphic courtesy of BackBlaze.com
I have had a lot of attention on this over the last while as the problem grows and have done extensive research on various ways of dealing with it so that if the worst case scenario happens to a client I can get them back up and running with no loss of data and minimal loss of time. To that end I have worked out a few different plans that will make this happen and allow you a full recovery should you become a target of ransomware.
I implement a backup solution developed by BackBlaze that runs on both Macs and PCs that runs a continuous, near-live backup to the cloud so that within a short time any changes you have made are effortlessly backed up.
In the event of a ransomware attack, it is possible that files that are corrupted are also backed up, potentially overwriting the originals in the cloud backup. THIS IS NOT A PROBLEM! Multiple versions of the files are kept in the cloud for up to 30 days. So if someone does get hit with a ransomware attack – and even if the corrupted files are backed up, overwriting the originals – one can roll back the clock and recover the original clean data from a previous point in time.
If you want more information on ransomware and it’s effects and mitigation I suggest reading these two posts on the BackBlaze website:
https://www.backblaze.com/blog/complete-guide-ransomware/
https://www.backblaze.com/blog/data-backup-minimizing-impact-ransomware/
Sure we’re paranoid – but are we paranoid enough?
Sometimes ransomware will additionally corrupt operating system files, rendering the computer itself unusable. In such a case merely recovering your user documents that have been stored in the cloud WILL NOT BE ENOUGH! If a computer has been infected the first step to recovery is to remove the malware from your system. If that can be done and guaranteed that the infection is gone, then recovering your data from the Cloud can occur and you are back in business.
However, IF your computer system itself is corrupted and/or the infection cannot be removed fully without a full wipe of the hard drive, then you have a machine that is unusable, even when you get your user files restored from the Cloud. In such a case as this only a re-installation from scratch or restoration from a full hard drive backup will do.
My solution for this situation is to create a full copy (known as a disk image) of your hard drive. This is a point in time snapshot of your computer which can be used as a starting point in case a full recovery is needed. This disk image will be stored in the Cloud as well, but using a different method then the live file backup software. Since the disk images are stored in the Cloud through a different configuration not directly accessible to the end user there is no danger they will be infected.
So the disk image gives us a base point in time to start with and the live backup software runs continuously to keep any file changes backed up. In the event of a ransomware attack we would first try to get rid of the infection, then recover the data files from the cloud backup. If for some reason the infection could not be removed or it had corrupted the Operating System beyond recovery, then we would re-image the hard drive using the previously created snapshot, run whatever updates were required for the Operating System and then use the live backups to update all the files to their latest versions. Full recovery.
This is also applicable to a situation such as a hard drive failure on the computer. A new hard drive can be acquired and the same full recovery procedure applied to it.
So with this two-pronged approach to a full backup system we can guarantee full recovery of a users computer system AND current data in the event of nearly ANY* type of disaster: ransomware, hard drive failure, theft and destruction of the computer and environment.
*Note: Hard drive images can only be used to run the same computer or one of similar specifications. However all data on the image can be recovered if needed.
The Solution
Regardless of what your business or personal computing habits, no one is fully immune to the various threats of modern day computing. Even the safest user with all the security products available can’t prevent the inevitable failure of the hard drive itself. So a comprehensive backup solution that takes into account the worst-case scenario is strongly recommended.
There are two backup packages to choose from with this configuration.
Option 1: The FULL disk image ‘paranoid’ level backup procedure as described above requires an in-person visit to image the hard drive and install and configure the live backup software. Disk images are then taken off-site and uploaded to the cloud.
Option 2: If distance or timing is an issue then the second option is to do a remote installation of the live backup software. This won’t allow for a full hard drive recovery from a catastrophic failure but at least all critical user data files will be backed up to the cloud continuously. With the relatively cheap cost and availability of cloud based storage solutions it is easy to give everyone a safety net no matter where they are and this is the minimum level of backup protection I recommend in today’s environment.
These packages are designed for single users and small offices. If your situation is different then a comprehensive backup plan can be created to fit your specific needs.
Sean Ford
Xpedient Technologies